Spear phishing is a targeted email or electronic communication scam crafted to appear legitimate.
Detecting a spear phishing message can be difficult without the appropriate knowledge due to the amount of personalized data acquired through the open web, Data Brokers, and People Search Sites. This article intends to provide you with everything you need to know to reduce your risk of being a spear phishing victim. Perhaps there is no sure way to prevent phishing or spear phishing, but we can learn from each other and create a more secure environment for ourselves and others.
Let us begin with distinguishing spear phishing and phishing.
Spear Phishing vs. Phishing: Understanding the Differences
Phishing messages are unsolicited (usually email) messages sent to a broad audience containing malicious links. This link, when clicked on, often leads to a website where the users are prompted to enter personal information. The attacker then uses this information for malicious purposes.
Spear phishing, on the other hand, is an attack that targets an individual or a small number of people. The attackers often use publicly available information from Data Brokers and People Search Sites to learn more about their target.
The table below compares phishing and spear phishing using eight markers: definition, target, attack volume, attack success, personalization (level), content, detection, and prevention.
| Marker | Phishing | Spear Phishing |
|---|---|---|
| Definition | Unsolicited emails aimed at a broad audience | Targeted emails aimed at a specific individual |
| Target | Random or mass targets | Specific individuals or organizations |
| Attack volume | High | Low |
| Attack success | Low to moderate | High |
| Personalization | Low | High |
| Content | Generic, mass-market message | Highly tailored message specific to the target |
| Detection | Can be detected by spam filters | Is more difficult to detect |
| Prevention | User education and spam filters | User education and more robust security measures |
Spear phishing is much more effective as an attack method because of the amount of personal detail and careful crafting that goes into it. As such, recipients must be extra diligent, carefully reviewing any email that requests personal or professional information.
The growth of phishing has been exponential. According to the FBI’s Internet Crime Complaint Center (IC3), reported phishing cases grew 184%, nearly tripling in just three years, from 114,702 to 323,972 cases in 2021. [1]
Spear phishing attacks have risen exponentially. According to a 2021 report from Barracuda Networks, spear phishing attacks increased by 667% from the end of 2019 to the end of 2020. [2]
Real-Life Phishing and Spear Phishing Examples
To help illustrate the types of techniques used by attackers, it is helpful to look at real-life examples of phishing and spear phishing emails. In this section, we will take a look at several examples. As you read this section and examine the messages, remember the common traits of phishing and spear phishing emails in the future.
Example #1: Phishing
In the first example, the annotator does an excellent job of pointing out the signs of potential phishing, including:
- Bad grammar, sentence structure, and spelling
- Blind carbon copied (BCC)
- Formatting errors
- Illegitimate URLs
- Lack of personalization
- Scare tactics
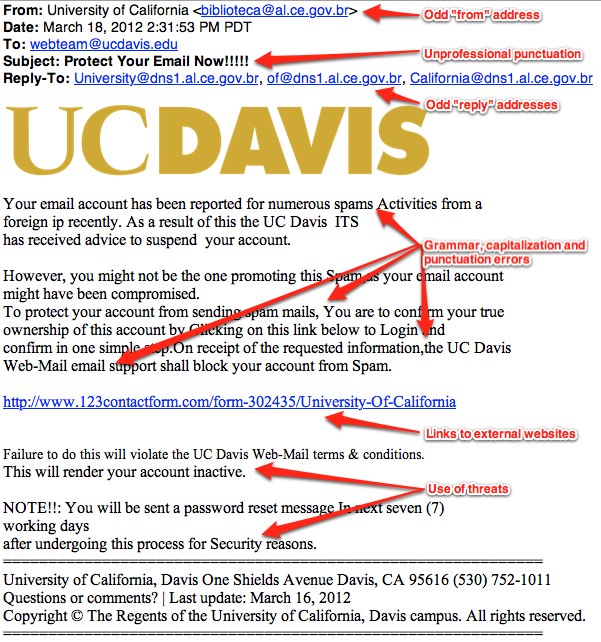
Example #2: Phishing
The following example is a rather sharp phishing email that could easily be mistaken as accurate. However, there are two subtle signs of phishing if one looks carefully. Look at the following example and see if you can spot them.
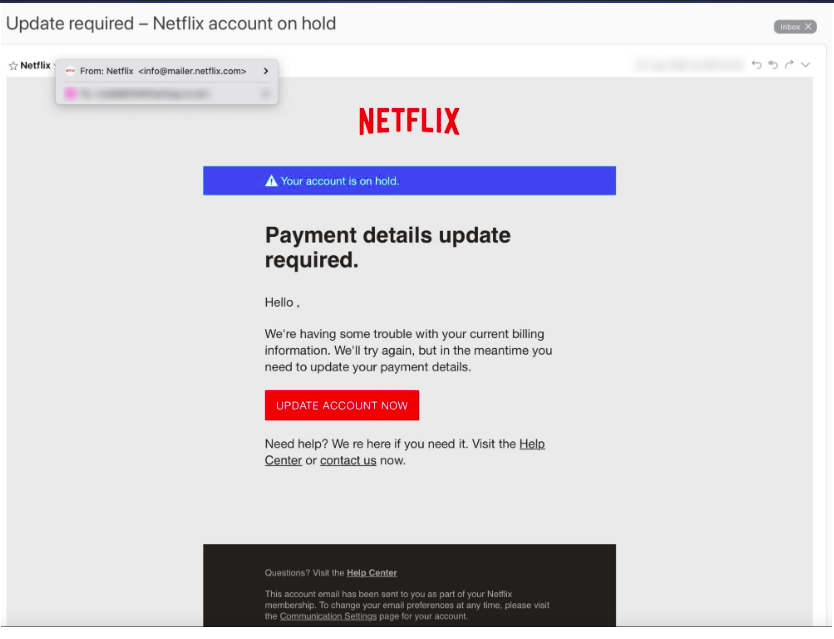
This one is not that easy. The first sign of phishing is the bad URL; “[email protected]” is not a real site. (Netflix will always send customer emails using the domain “@netflix.com”).
The second sign of phishing is a formatting error after “Hello” and before the comma. But again, there’s a lack of personalization here that is common in most phishing emails.
Example #1: Spear Phishing
Take a look at our first spear phishing example.
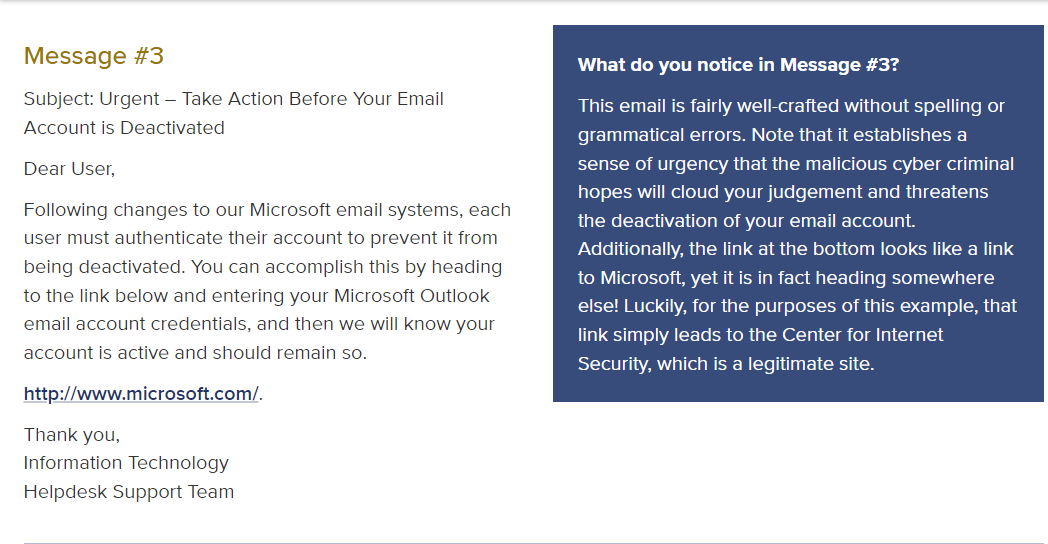
First, notice the absence of spelling and grammar errors. The message smartly employs social engineering in its creation of a sense of urgency, which is more subtle. There are two potential signs of phishing here.
First, the message is not personalized, but this occasionally happens in a spear phishing email.
Second, in the digital version of this message, the URL before the sign-off does not direct to Microsoft’s site. (Hovering your mouse over a URL to ensure that the URLs match is a simple way to avoid redirection to a malicious site.)
Example #2: Spear Phishing
Here’s our second and final spear phishing example. Let’s take a look.

There’s not much to go by here regarding obvious crafting mistakes. The message is well-written as well. Moreover, the social engineering here is subtle yet effective in that the urgent tone is not excessive.
If Kevin were able to take more than a cursory look at the message, he might ask himself the following questions:
- If the CEO needed something done within the hour, why was he sending an email? The semi-formal language and the informal greeting and sign-off indicate that the two men know one another. In such a case, a or text would be more appropriate.
- Why is there an attached file with no contact information? The former is certainly more confidential than the latter. It benefits Chris to include all necessary information in a single message, especially given the supposed time constraints.
Quick Questions to Spot Spear Phishing
There are additional questions one can ask as a “framework” for detecting potential spear phishing:
- Do I know the sender?
- If yes, does the tone of the email unusual, given the supposed sender?
- Does the email contain any unusual requests?
- Can I independently verify the email’s content?
- Is there a precedent for this type of request within the organization?
To better mitigate the risks of spear phishing, prioritize the scanning, removal, and monitoring of PII exposure.
Anatomy of a Spear Phishing Attack: How Attackers Trick You
Spear phishing attacks usually follow a typical, repeated sequence of six stages, five of which involve the target. The five stages are reconnaissance, email creation, delivery, click, and compromise. “Covering tracks” is a post-attack process attackers follow to evade detection.
| Stage | Description |
|---|---|
| Reconnaissance | The attacker identifies the target and gathers information about the individual, such as their name, job title, and contact information. This information may be collected from public sources, social media profiles, or other online sources. |
| Message creation | The attacker crafts an email designed to look legitimate and entice the target to take action. The attacker employs social engineering tactics and personal details to convince the target to open a malicious attachment or click on a link. |
| Delivery | The attacker sends the email to the target using a spoofed email address to make it appear that the email is from a trusted source. |
| Click | The personalized nature of the email tricks the target, and they click on the link or open an attachment. This may result in installing malware on the target’s computer, stealing sensitive information, or other nefarious activities. |
| Compromise | Once the attacker has gained access to the target’s system or information, they may use this access to further their attack or carry out additional malicious activities, such as stealing login credentials or installing other malware. |
| Covering tracks | Finally, the attacker covers their tracks to avoid detection, such as deleting logs or erasing evidence of their activities. |
The Aftermath of a Successful Spear Phishing Attack
Falling victim to a spear phishing attack is potentially devastating. Some of the adverse results of a successful spear phishing attack include the following:
- PII theft or loss: Personally Identifiable Information (PII) is any data that can be used to identify a person. Attacks may seek to acquire PII, including credit card details, login credentials, and Social Security numbers. With this information, the attacker may commit identity theft or some other type of fraud.
- Financial loss: Besides financial losses arising from unauthorized credit card or financial account use, it is common for the victim of a spear phishing attack to incur indirect financial losses. These include credit score damage, legal fees, and device replacement.
- Emotional distress: Given what’s at stake in a spear phishing attack, it is normal to feel inner turmoil if one becomes a victim. This is especially true if the attack resulted in financial losses, identity theft, or other serious consequences.
The Role of Data Brokers and People Search Sites in Spear Phishing
In no unclear terms, Data Brokers and People Search Sites help to fuel spear phishing. Both extract and aggregate massive amounts of PII from across the web and make it widely available to potential attackers. As such, both entities increase the risk of spear phishing and its effects, including identity theft, financial fraud, and other types of cybercrime.
What are Data Brokers?
Data Brokers have built a $250 billion industry collecting, packaging, and selling your data. Several Data Brokers have been found guilty of crimes, suffered a data breach, or both. The credit bureau Equifax may be the best example of what can go wrong if companies can gather and sell your data unchecked.
Equifax, one of the three credit bureaus and a massive Data Broker, was breached in July 2020. The result? The exposed PII of over 147 million Americans. The data leaked included Social Security numbers, dates of birth, driver’s license numbers, credit card details, and other personal data.
When they’re not being breached or selling off your information, Data Brokers post their information to any number of online or offline databases.
Given the External Data Privacy risks that Data Brokers pose, partnering with a company that can scan for your PII and prompt Data Brokers for immediate removal is essential.
What are People Search Sites?
People Search Sites collect vast amounts of PII from across the web and post it to their online databases. Cyberattackers often use People Search Sites to acquire more personal information about their targets, such as contact information, job titles, employer names, social media profiles, and other data. Of course, this information often enables attackers to craft a more targeted and convincing email message.
Much information from People Search Sites and Data Brokers can be found via a simple Google search. Additionally, there are many websites dedicated to giving access to Data Broker information for free or at a very low cost.
Avoiding Spear Phishing Attacks
While it is true that spear phishing emails are effective, there are equally effective ways of spotting a spear phishing message. Here are five step-by-step actions to take after receiving an email:
1. Upon receiving the email, read its contents carefully and look for suspicious content.
2. Verify the sender’s identity by looking up their contact information
3. Check for any spelling or grammatical mistakes or links to any unfamiliar websites
4. Note any aggressive or overly urgent content within the email, as this is a common social engineering technique.
5. When in doubt, leave the email alone and consult with someone in your IT department.
You can more effectively mitigate the risks of spear phishing by scanning for, removing, and monitoring for PII exposure across more than 350 Data Brokers and People Search Sites.
Derisk your private data and perform a free privacy scan today!
References
[1] Federal Bureau of Investigation. Internet Crime Complaint Center(IC3) | Annual Reports. (2021). Retrieved February 24, 2023, from Ic3.gov website: https://www.ic3.gov/Home/AnnualReports
[2] Barracuda Networks. (2021). Spear phishing: Top threats and trends Vol. 2. Retrieved February 23, 2023 from https://www.barracuda.com/resources/reports/spear-phishing-report-vol2











